
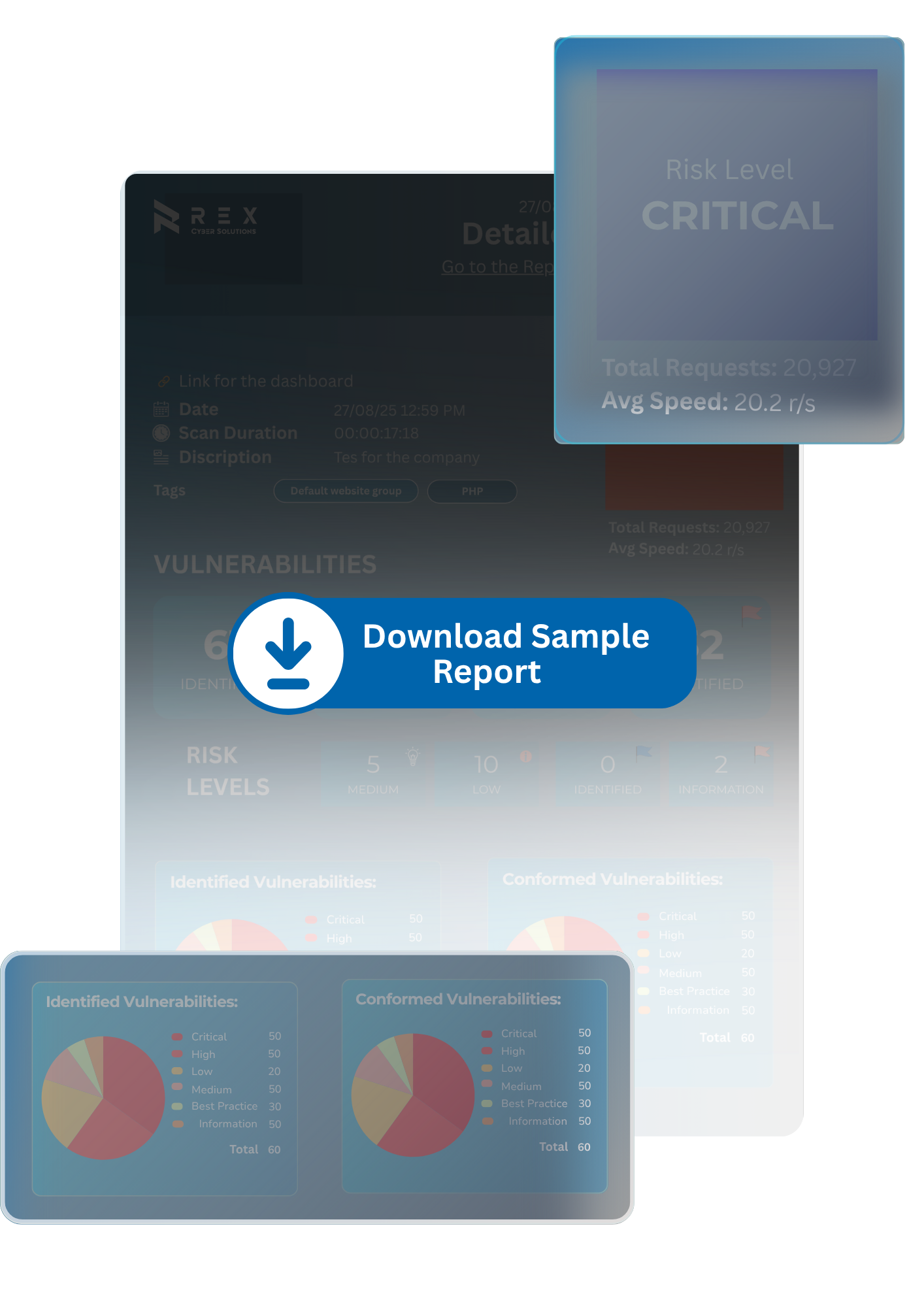
.png)



















.png)



















Unlike automated-only scans, our Secure Code Review combines manual intelligence with precision tooling to uncover deep flaws and strengthen your SDLC.
White Box testing examines a software's underlying structure, coding, and architecture in order to validate the input-output flow and improve the application's design, security, and utility. Testing of this kind is sometimes referred to as internal testing, clear box testing, open box testing, or glass box testing because testers can see the code.
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.
Grey box testing, which combines black box and white box testing, is a software testing approach used to test an application while only having a general understanding of its core code. It searches for and identifies context-specific errors that the application's poor code structure has produced.
Who Should Use Our Code Review Services

End-to-end visibility, guidance, and compliance-ready outputs
High-level, non-technical insights for CXOs, product heads, and stakeholders.
Detailed, developer-friendly list of flaws — with CVSS scores and exploit potential.
Step-by-step recommendations aligned with your stack and CI/CD pipeline.
Mapped to OWASP Top 10, PCI DSS, HIPAA, ISO 27001, and audit requirements.
Post-fix review of high-risk items to confirm issues are fully mitigated.
Why Leading Businesses Choose Us
Yes — automated tools often miss logic flaws, insecure flows, and misused cryptography. Our manual review fills those gaps.
Ideally during development and before each major release. Early review prevents expensive rewrites later.
Yes — we support Java, Python, .NET, JavaScript, PHP, and more. We adapt to your framework and codebase structure.
Absolutely. Secure Code Review supports ISO 27001, PCI DSS, HIPAA, and OWASP-based compliance controls.
No — our team works alongside your sprints and dev cycles to help you fix faster, not slower