
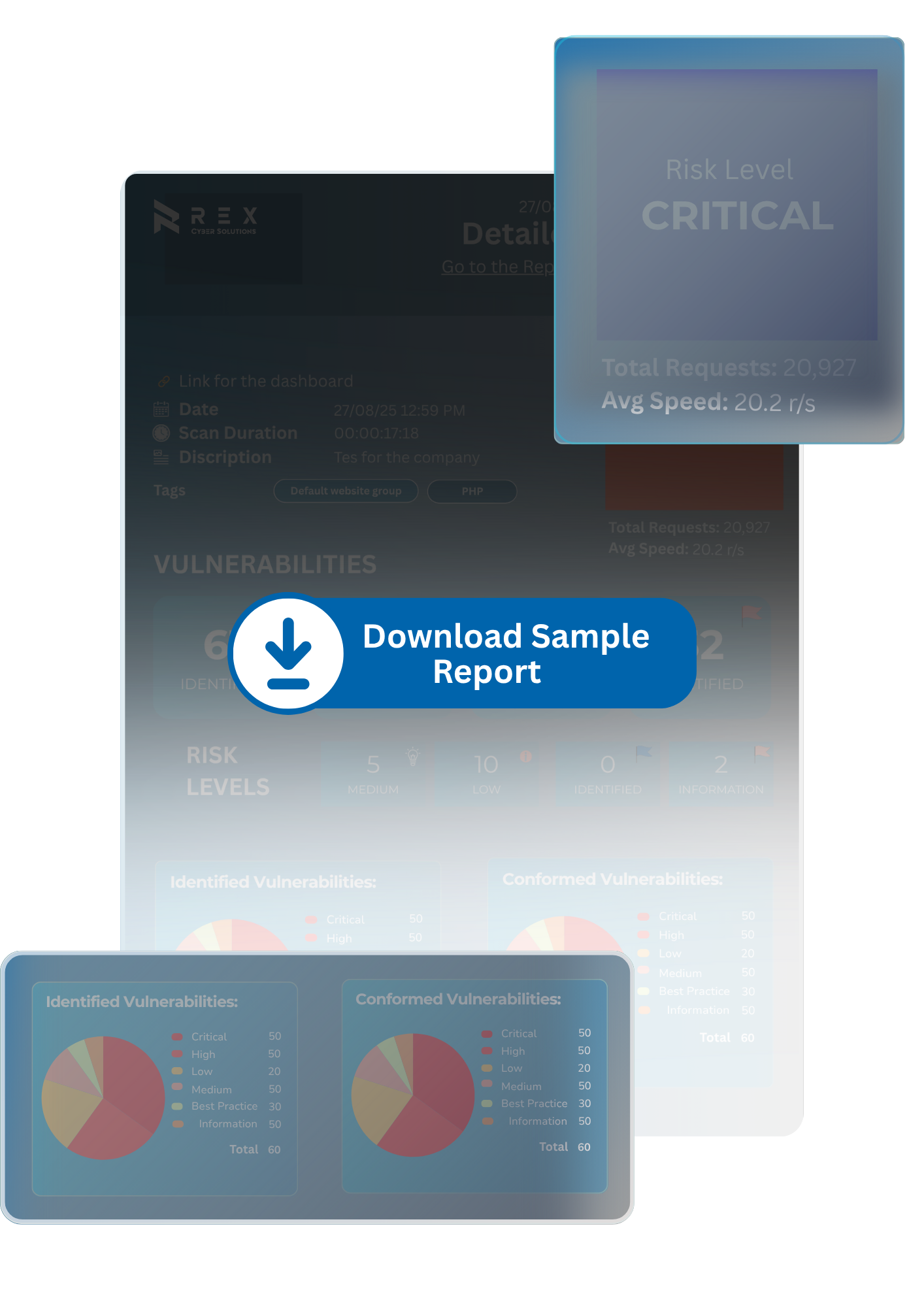
.png)



















.png)



















Our cloud security audit and configuration review covers all critical components of your cloud environment — across all major platforms and architectures.
White Box testing examines a software's underlying structure, coding, and architecture in order to validate the input-output flow and improve the application's design, security, and utility. Testing of this kind is sometimes referred to as internal testing, clear box testing, open box testing, or glass box testing because testers can see the code.
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.
Grey box testing, which combines black box and white box testing, is a software testing approach used to test an application while only having a general understanding of its core code. It searches for and identifies context-specific errors that the application's poor code structure has produced.
Real-World Studies of What Went Wrong

Every cloud object, account, and service reviewed
Understand which settings pose which business threats
Clear, ranked action items for your team or MSSP
One round of verification testing post-remediation
Ready-to-share summaries for auditors, CIOs, and compliance leads
Guidance and clarity at every step
Security That Aligns with Your Cloud Strategy and Compliance Goals
Defaults prioritize usability over security. They often allow broader access, incomplete logging, and unencrypted data by default.
Absolutely. We specialize in environments that span AWS, Azure, GCP, and on-premises systems.
Best practice is quarterly or biannual audits — especially after major deployments or policy changes.
Yes — we deliver prioritized remediation steps and support post-fix verification.
Typically within 5 business days of onboarding. Timeline varies based on environment size and complexity.