
.png)



















.png)



















We simulate real-world attacker tactics across your cloud assets — ensuring security where it matters most.
White Box testing examines a software's underlying structure, coding, and architecture in order to validate the input-output flow and improve the application's design, security, and utility. Testing of this kind is sometimes referred to as internal testing, clear box testing, open box testing, or glass box testing because testers can see the code.
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.
Grey box testing, which combines black box and white box testing, is a software testing approach used to test an application while only having a general understanding of its core code. It searches for and identifies context-specific errors that the application's poor code structure has produced.
Who Should Use Our Services
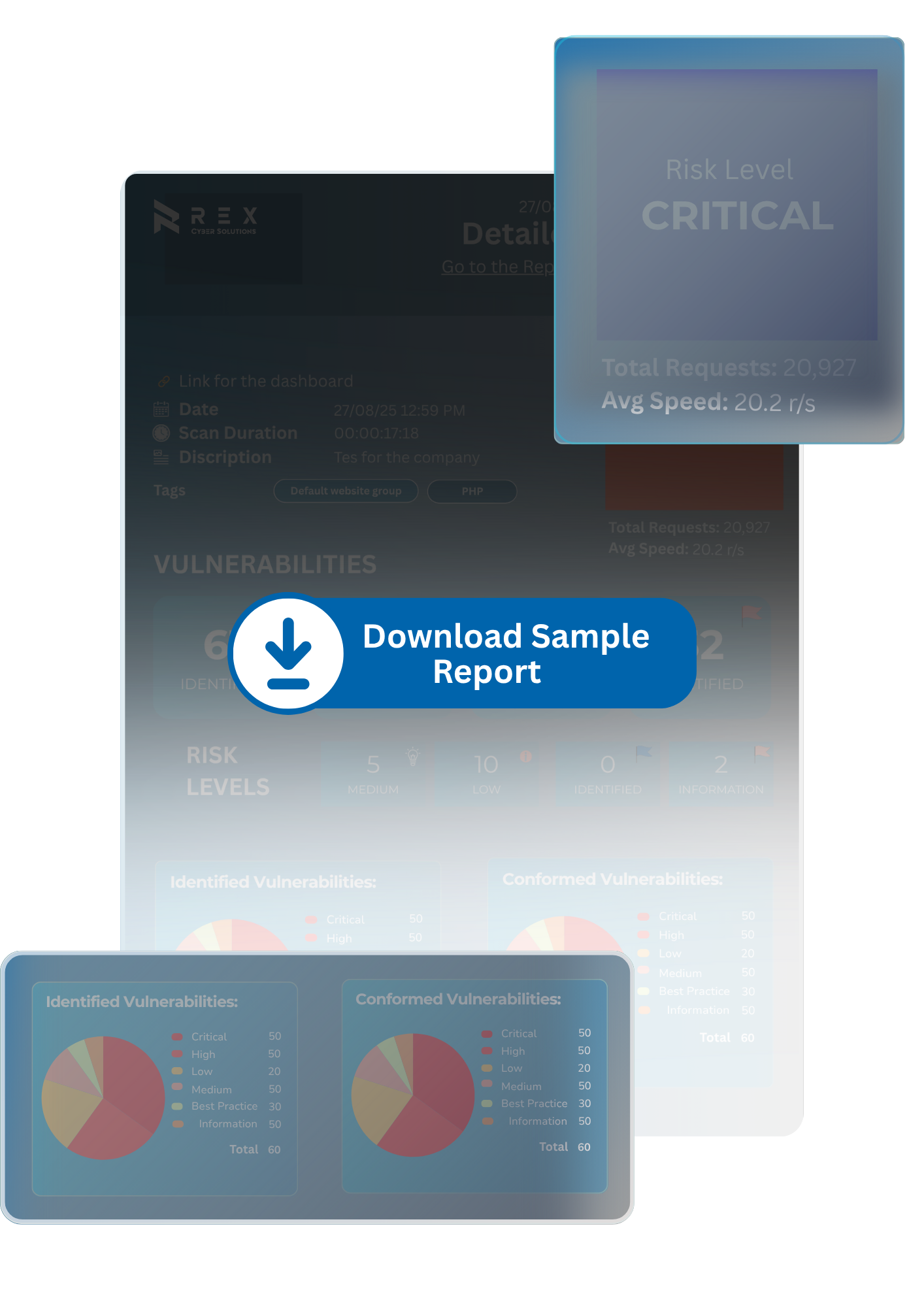
Summarized findings with direct business implications — ready for leadership and boardrooms
In-depth report on cloud-specific flaws: IAM, APIs, serverless, containers, and more
Each finding tied to operational, financial, and compliance risk levels
Clear, prioritized fix recommendations with architectural insights
One round of retesting to verify vulnerabilities are remediated
Single point of contact to guide you throughout the engagement
Who Should Use Our Services and how
Cloud testing targets IAM policies, APIs, containers, serverless functions, and misconfigurations — areas often missed by traditional methods.
No. Our methods are non-intrusive and coordinated with your team to ensure zero downtime.
Laptops, mobile phones, Wi-Fi cameras, guest devices, smart office tools — if it’s wireless, it’s tested.
Yes — we support AWS, Azure, GCP, and private or hybrid clouds.
At least annually — and after any major deployment or cloud architecture change.