
.png)



















.png)



















Unlike superficial scans, our Network VAPT simulates real-world threats — identifying technical vulnerabilities and translating them into business risk.
White Box testing examines a software's underlying structure, coding, and architecture in order to validate the input-output flow and improve the application's design, security, and utility. Testing of this kind is sometimes referred to as internal testing, clear box testing, open box testing, or glass box testing because testers can see the code.
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.
Grey box testing, which combines black box and white box testing, is a software testing approach used to test an application while only having a general understanding of its core code. It searches for and identifies context-specific errors that the application's poor code structure has produced.
Who Should Use Our Network VAPT Services

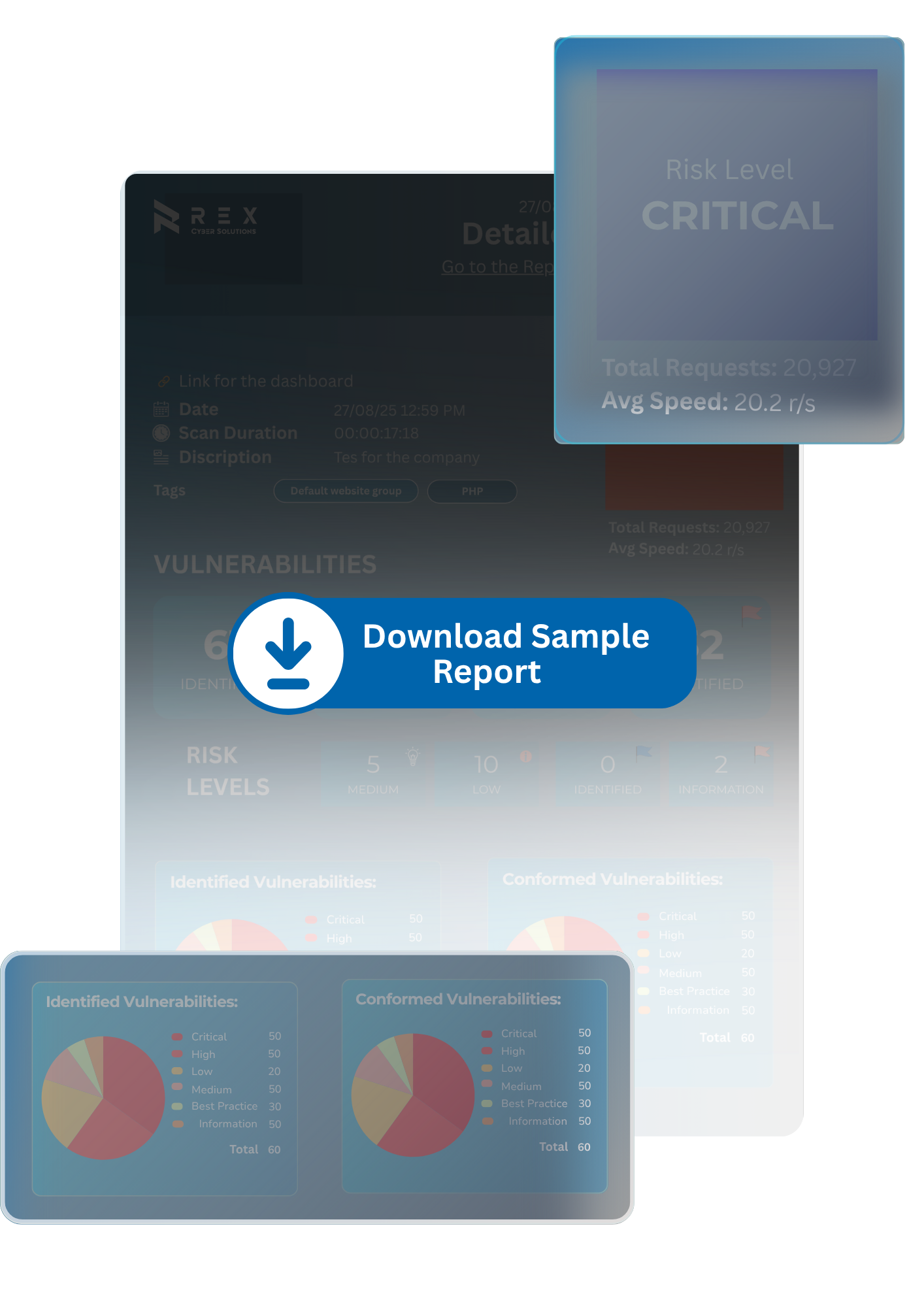
CXO-ready insights connecting vulnerabilities to business, financial, and compliance impact.
Technical findings including risk severity (CVSS), affected systems, and potential exploit paths.
Clear, actionable steps to fix vulnerabilities — prioritized by business risk.
Map findings and remediations to frameworks like ISO 27001, DPDP, SOC 2, PCI DSS, and HIPAA.
One round of Validation testing to validate fixes and demonstrate security maturity.
Direct call with a certified security expert to walk through the report and assist with remediation strategy.
Why Leading Businesses Choose Us
No. Scanning is surface-level. Our VAPT includes manual exploitation and full attack simulation — just like real hackers do.
Annually at minimum, and after major infrastructure changes, cloud migrations, or security incidents.
Yes. ISO 27001, DPDP, PCI DSS, HIPAA, and others require periodic testing of security controls. VAPT validates these controls.
Absolutely. We perform hybrid assessments across on-premise, cloud (AWS, Azure, GCP), and containerized environments.
No. We plan and coordinate testing to avoid disruptions, focusing on safe, non-intrusive techniques.
Typically 3–7 working days depending on the number of IPs, devices, and scope of systems.