
.png)



















.png)



















More than scans — we simulate real-world attacker behavior to reveal hidden risks in your wireless infrastructure.
White Box testing examines a software's underlying structure, coding, and architecture in order to validate the input-output flow and improve the application's design, security, and utility. Testing of this kind is sometimes referred to as internal testing, clear box testing, open box testing, or glass box testing because testers can see the code.
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.
Grey box testing, which combines black box and white box testing, is a software testing approach used to test an application while only having a general understanding of its core code. It searches for and identifies context-specific errors that the application's poor code structure has produced.
Who Should Use Our Services and how

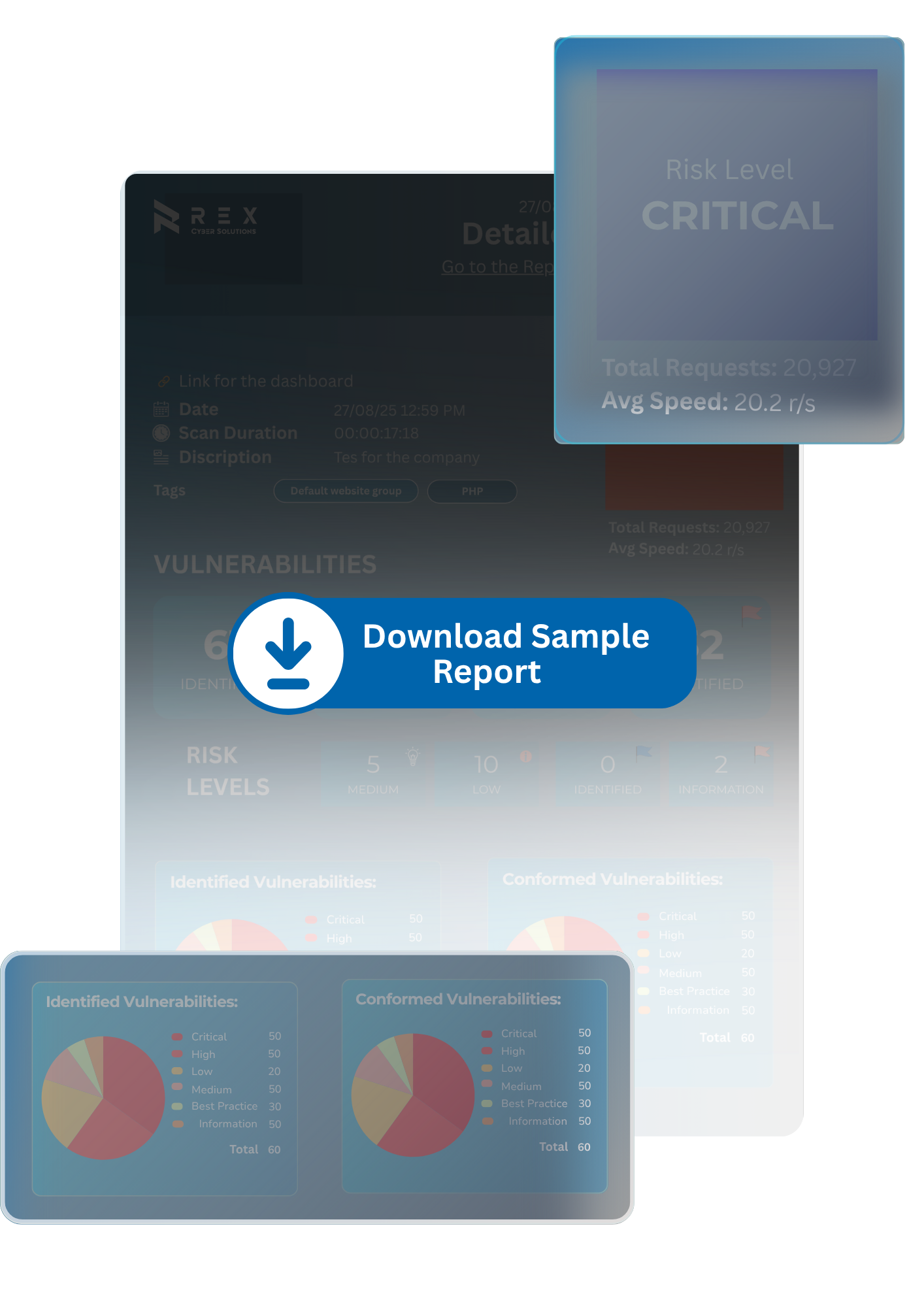
Boardroom-level summary with clear business impact mapping
Full detail on SSIDs, rogue devices, WPA weaknesses, and segmentation flaws
Unseen or insecure devices documented and scored
Custom fix recommendations for IT and network teams
Assures risks are closed and network hygiene is restored
One-on-one with our wireless security lead to review findings and next steps
Who Should Use Our Services and how
Firewalls don’t stop attackers already connected to your internal Wi-Fi. Wireless is the modern backdoor.
Yes — both frameworks mandate secure network access. Our reports align with audit standards.
Laptops, mobile phones, Wi-Fi cameras, guest devices, smart office tools — if it’s wireless, it’s tested.
Yes. Signal bleed makes it possible. We measure it, map it, and help fix it.
Kickoff in 48 hours. Completion in 3–7 business days.