
.png)



















.png)



















We don’t just scan — we emulate attacker behavior to uncover real-world risks in your mobile app ecosystem.
White Box testing examines a software's underlying structure, coding, and architecture in order to validate the input-output flow and improve the application's design, security, and utility. Testing of this kind is sometimes referred to as internal testing, clear box testing, open box testing, or glass box testing because testers can see the code.
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.
Grey box testing, which combines black box and white box testing, is a software testing approach used to test an application while only having a general understanding of its core code. It searches for and identifies context-specific errors that the application's poor code structure has produced.
Who Should Use Our Services and how

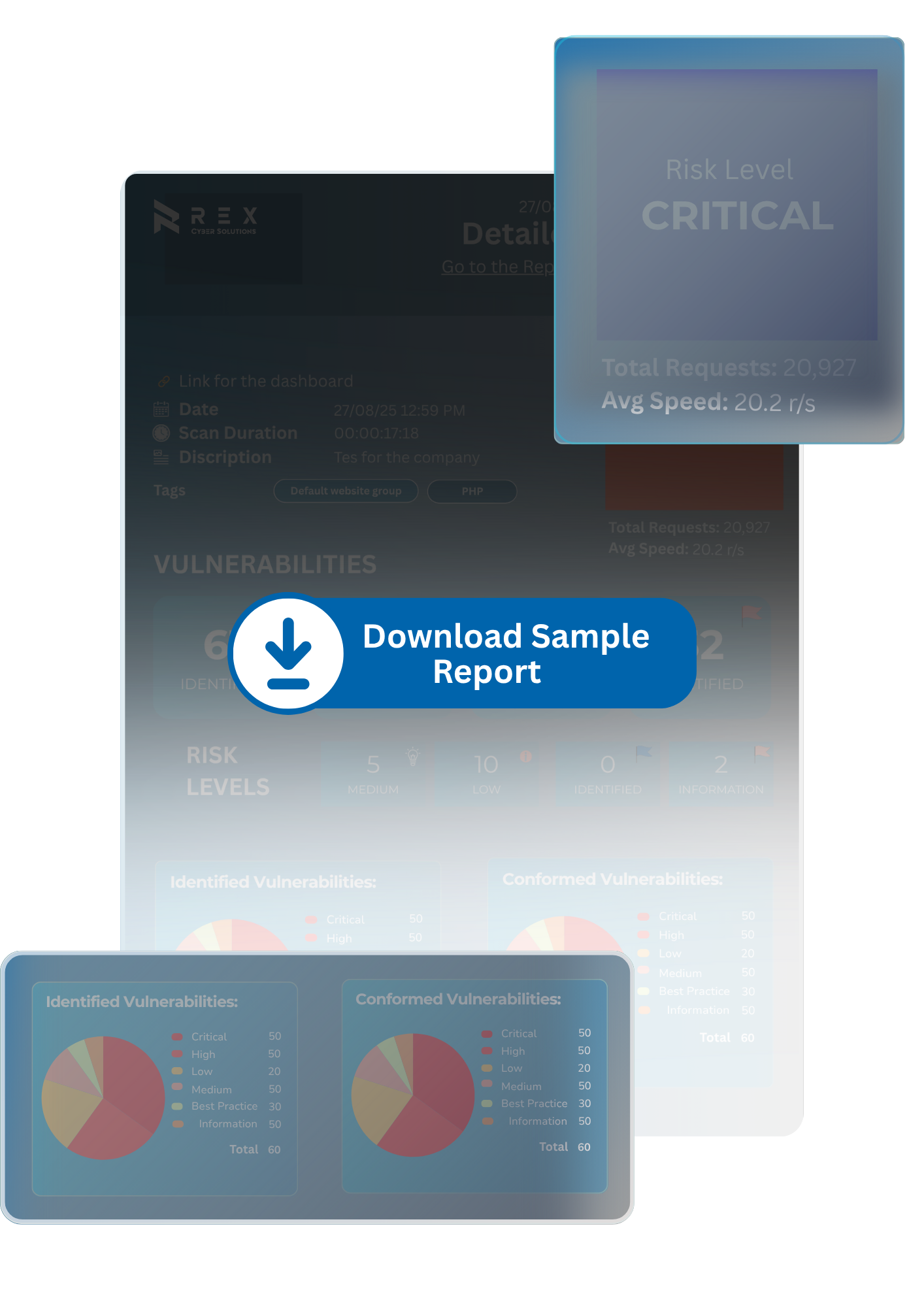
C-suite ready overview that maps findings to business impact.
Full details on insecure APIs, code flaws, permissions abuse, and platform-specific risks.
Prioritized, developer-friendly fixes based on risk and severity.
Classifies vulnerabilities with severity and potential exploitability.
Post-fix validation included to confirm security maturity.
Walkthrough with our application security expert to debrief teams and plan next steps.
Who Should Use Our Services and how
We recommend at least once a year or after any major code release or backend update.
No. Our testing is non-intrusive and conducted in pre-production or with safe techniques in live environments.
Yes. We assess both platforms with device-specific and OS-specific attack vectors.
Absolutely. Our report includes insights to help meet app store security policies.
We analyze these components for risks and provide clear insights on what needs patching or replacement.