
.png)



















.png)



















Unlike traditional “scan-and-forget” services, our Web Application Penetration Testing (WAPT) delivers business-aligned insights tailored to your risk profile.
White Box testing examines a software's underlying structure, coding, and architecture in order to validate the input-output flow and improve the application's design, security, and utility. Testing of this kind is sometimes referred to as internal testing, clear box testing, open box testing, or glass box testing because testers can see the code.
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.
Grey box testing, which combines black box and white box testing, is a software testing approach used to test an application while only having a general understanding of its core code. It searches for and identifies context-specific errors that the application's poor code structure has produced.
Who Should Use Our Services...

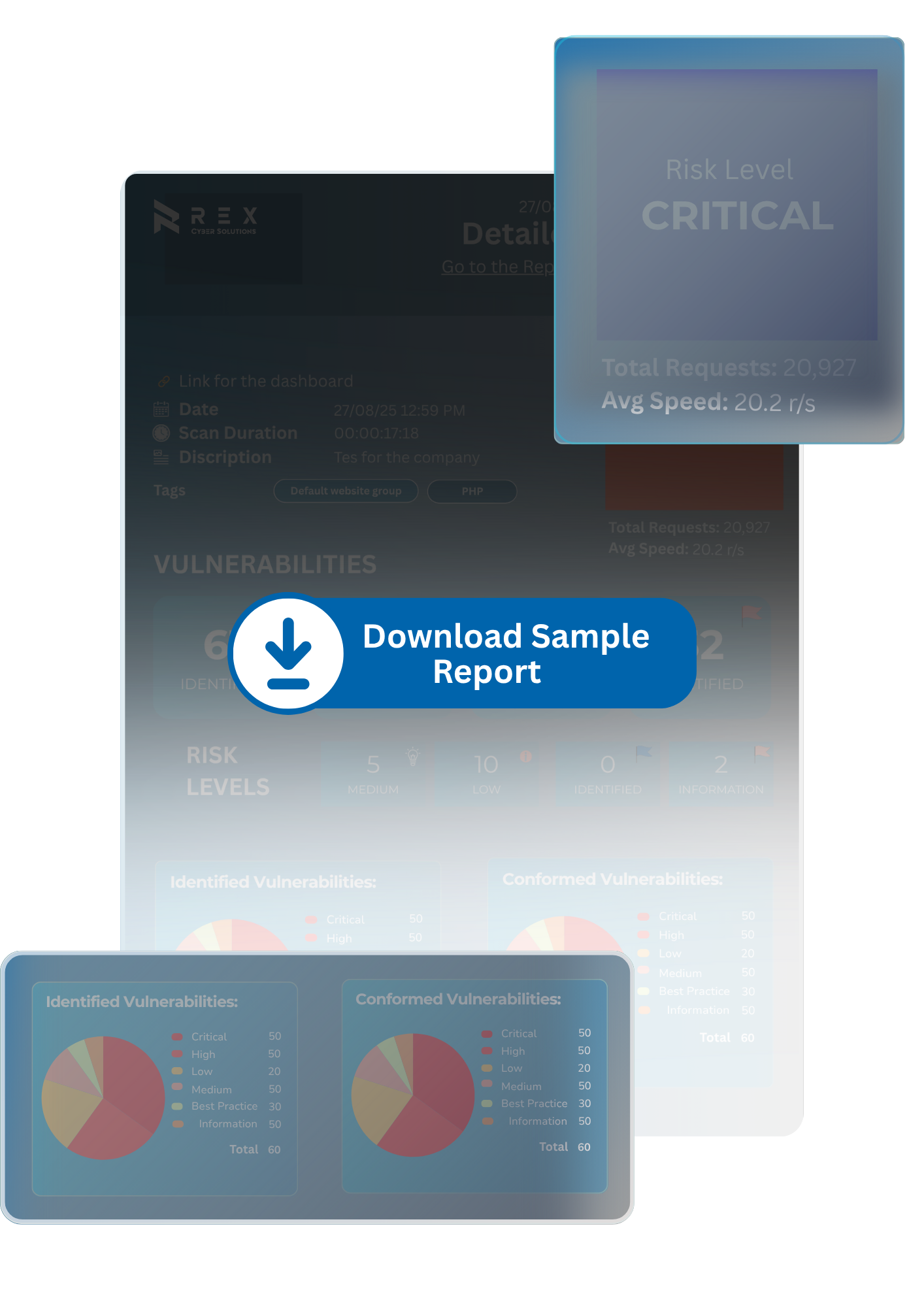
A high-level, non-technical overview outlining key risks and business impact, tailored for decision-makers.
A comprehensive technical document mapping all identified security flaws with severity ratings.
Step-by-step recommendations and best practices to help your development team fix vulnerabilities effectively.
Each finding is assigned a score based on its potential impact on revenue, operations, and compliance.
We re-test resolved issues to confirm successful remediation and eliminate residual risk.
Direct consultation with a security expert to walk through findings and answer technical or strategic questions.
Who Should Use Our Services and how
No. Our testing is designed to be non-intrusive and controlled, with full coordination to avoid downtime or user disruption. We can schedule tests during off-peak hours if needed.
You’ll get a detailed technical report, an executive summary for stakeholders, prioritized risk scores, and developer-ready remediation steps. We also include a retesting round after fixes.
Yes. Firewalls and plugins provide surface-level defense, but WAPT identifies deeper, often overlooked vulnerabilities inside your custom code and business logic — where real risk resides.
We recommend conducting WAPT at least once a year, or after any major code changes, feature releases, or compliance requirement updates — to maintain a strong security posture.
Yes. Our penetration testing aligns with major compliance standards including ISO 27001, DPDP, SOC 2, and HIPAA, and we provide documentation that supports your audit process.